Cybersecurity Monthly Report (November 2023)
Ex ante joint defense and monitoring
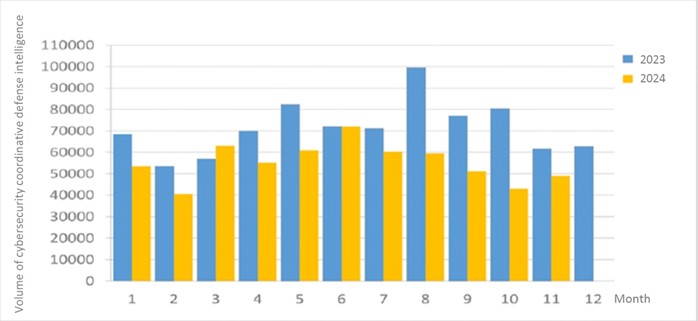
A total of 49,099 pieces of government agency cybersecurity joint defense intelligence were collected this month, analyzing the types of identifiable threats. The top three identifiable threats were information collection (47%), i.e., mainly obtaining information through attacks such as scanning, detection and social engineering, followed by intrusion attempts (27%), i.e., mainly attempts to hack unauthorized hosts; and intrusion attacks (11%), most of them involving unauthorized access to systems or acquisition of system/user privileges. In addition, the distribution of intelligence volume in the past year is as shown in Figure 1.
After further compilation and analysis of joint defense intelligence, it was found that hackers recently sent social engineering e-mails containing click-tracking links and malicious short URLs. By feigning relevance to the agency's business, they tricked agency personnel into opening suspicious links and downloading malicious files, thus conducting social engineering e-mail attacks on government agencies. The relevant information has been provided to agencies with recommendations for joint defense, monitoring and protections.
In-process reporting and responding
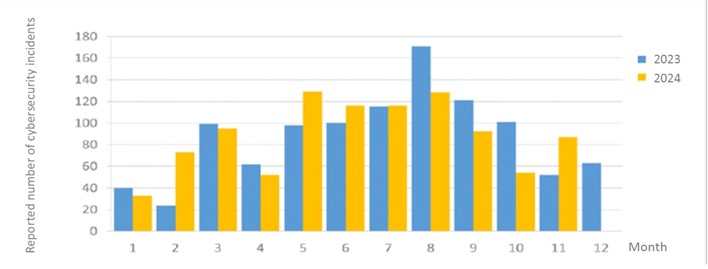
There were a total of 86 information security incident reports this month, an increase of 65.38% from last year. The National Institute of Cyber Security detected that some information devices from multiple agencies attempting to download malicious programs or connecting to seemingly malicious programs. This accounted for 39.53% of the total number of reports, and after investigation by the reporting agency above, it was found that the abnormal connections were from a surveillance device. In addition, the statistics of cybersecurity incident reports in the past year are as shown in Figure 2.
Post information sharing
This month, it was detected that the official document system of a certain agency downloaded malicious xml files online. Upon examination, researchers from the National Institute of Cyber Security found it to be related to a major vulnerability (CVE-2023-46604, CVSS Score 10), as disclosed by Apache ActiveMQ in October, and immediately issued a cybersecurity alert to notify the agency in question. The agency in question originally said that the hacked system did not use the aforementioned software, but after further inspection by the maintenance vendor, it was found that the functional module of the system did use the ActiveMQ protocol, and its version was within the scope of major vulnerabilities. The agency in question has since received assistance in updating the software.
It is common for government websites to use third-party bundles and software to develop system functions or services, thereby shortening the website construction time. However, third-party bundles or software may also come with security vulnerabilities. It is recommended that organizations inventiry and pay attention to the bundles or software used on their websites, and through regular inspections, vulnerability scanning, and other security tests, keep track of system version updates and security status to patch vulnerabilities in a timely manner. If, for some reason, the vulnerability cannot be patched in time (such as the original vendor has yet to release an updated version), relevant protective measures should be taken immediately to reduce the risk of the vulnerabilities being exploited, and causing the website to be invaded.