Cybersecurity Monthly Report (September 2023)
Ex ante joint defense and monitoring
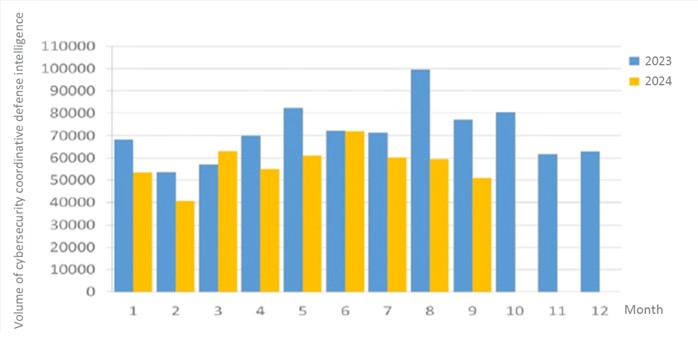
A total of 51,086 pieces of government agency cybersecurity joint defense intelligence were collected this month, analyzing the types of identifiable threats. The top identifiable threat was information collection (47%), i.e., mainly obtaining information through attacks such as scanning, detection and social engineering. This was followed by hacking attempts (25%), which were mainly attempts to hack unauthorized hosts; and intrusion attacks (13%), most of them involving unauthorized access to systems or acquisition of system/user privileges. In addition, the distribution of intelligence volume in the past year is as shown in Figure 1.
After further compilation and analysis of joint defense intelligence, it was found that hackers have recently abused the Cloudflare R2 cloud storage service by setting up phishing websites and sending social engineering e-mails to attack devices of government agencies and the general public. Cloudflare R2 provides free website hosting services. As a result, the hackers hosted phishing websites on Cloudflare R2 which they inserted the government agency domain name after the phishing website URLs. They then submitted applications with falsified business information to conduct social engineering attacks. The relevant information has been provided to agencies with recommendations for joint defense, monitoring and protections.
In-process reporting and responding
A total of 94 cybersecurity incident reports were submitted this month, a decrease of 22.31% compared with the same period last year. This was mainly due to reduction in the number of reported cases during actual military exercises, which decreased by approximately 36.07% compared with the same period last year. In addition, the statistics of cybersecurity incident reports in the past year are as shown in Figure 2.
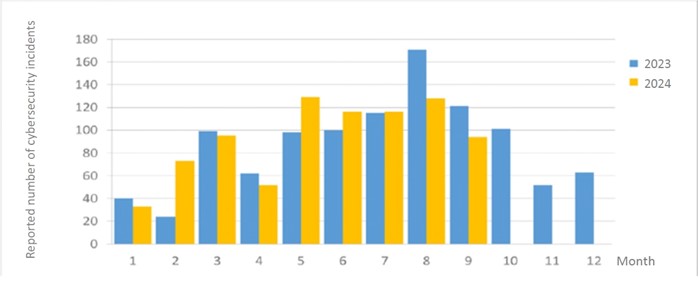
Figure 2 Number of reported cybersecurity incidents
Post information sharing
This month, the National Institute of Cyber Security detected routers or firewalls of a certain brand used by some agencies attempting to download a Trojan horse program, HiatusRAT, in June 2023. Malicious program connection consistent with HiatusRAT network device was still found this month. Upon investigation, the storage log of the network communication equipment of the previous agency was unable to confirm the cause of the incident due to limited storage space. Although improvements were made by resetting and updating the firmware, continuous monitoring revealed that hacking still seemed to be undergoing. As such, the agency has replaced the network communication equipment and expanded the available storage capacity to store logs for more than six months.
Network equipment often has limited storage space for log records, making it impossible to further clarify the cause of incidents. Although the agency has taken measures such as resetting and updating firmware to fix security vulnerabilities, it still cannot ensure that the updated firmware can effectively prevent attacks. When a cybersecurity incident occurs, a root cause analysis should be performed to undertake vulnerability patching, strengthening actions, and improvement measures. If the cause of the incident cannot be confirmed due to insufficient device storage space, aside from strengthening equipment security protection measures and detection mechanisms, it is also recommended to expand the log storage space (such as setting up a separate log server). The implementation of protective measures such as strengthening log checking or inventory of network equipment can facilitate subsequent investigations of the cause of incidents and reduce the risk of repeated intrusions.