Cybersecurity Monthly Report (July 2024)
Ex ante joint defense and monitoring
A total of 76,572 pieces of government agency cybersecurity joint defense intelligence were collected this month (an increase of 5,931 from the previous month). Analyzing the types of identifiable threats, the top identifiable threat was information collection (43%), i.e., mainly obtaining information through attacks such as scanning, detection, and social engineering. This was followed by intrusion attacks (22%), most of them involving unauthorized access to systems or acquisition of system/user privileges; and hacking attempts (19%), which were mainly attempts to hack unauthorized hosts. The distribution of intelligence volume in the past year is as shown in Figure 1.
After further compilation and analysis of joint defense information, it was discovered that hackers had recently sent social engineering e-mails with the subject line “Salary Assessment Notification” and with the content announcing a pay raise in order to attack government agencies. Upon inspection, it turned out that the hackers exploited a redirect vulnerability of the American Institute of Aeronautics and Astronautics website and embedded a phishing URL to trick recipients into clicking on the link and submitting sensitive information. The relevant information has been provided to agencies with recommendations for joint defense, monitoring and protections.
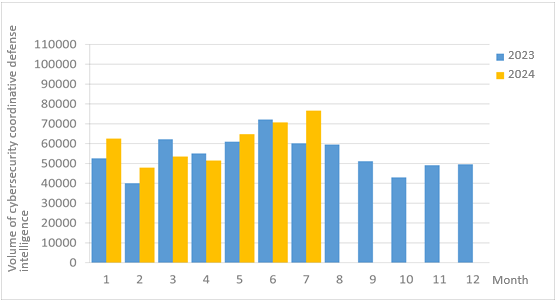
Figure 1 Statistics of cybersecurity monitoring intelligence in joint defense
In-process reporting and responding
The number of cybersecurity incident reports totaled 276 this month (an increase of 124 from the previous month), representing a 1.37-fold increase compared to the same period last year. This is mainly due to the relatively high number of successful attacks related to this month’s military exercises, predominantly related to ineffective access control, dangerous or outdated components, and encryption mechanism failures. The attacks accounted for 61.59% of the total number of reports this month. The statistics of cybersecurity incident reports in the past year are as shown in Figure 2.
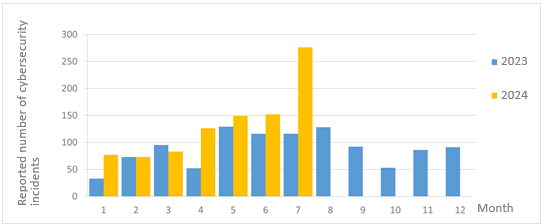
Figure 2 Number of reported cybersecurity incidents
Post information sharing
This month, a certain government agency was informed by users that an application form on its official website could not be downloaded properly. Upon investigation, it was discovered that the vendor responsible for maintaining the website had only performed standalone testing after fixing vulnerabilities on the website, without performing regression testing. As a result, the vendor did not realize that the patch affected the existing functionality of the website and caused the file download feature to stop working. The website maintenance vendor has already made adjustments and will test various features of the website before the new version of the website is released.
Additional Reference:
According to the schedule of the Regulations on Classification of Cyber Security Responsibility Levels, government agencies are required to conduct security testing, including vulnerability scanning and penetration testing, to detect and fix website vulnerabilities in a timely manner. It is recommended that testing plans and emergency response procedures be developed in advance for all patching and remediation activities. In addition, records should be kept after testing is completed to facilitate follow-up actions or audits. For systems in operation, regression testing should be prioritized to ensure that existing functionality has not been compromised.