Cybersecurity Monthly Report(January 2024)
Ex ante coordinative defense and monitoring
A total of 62,578 pieces of government agency cybersecurity coordinative defense intelligence were collected this month (an increase of 12,997 from the previous month), analyzing the types of identifiable threats. The top identifiable threat was information collection (31%), i.e., mainly obtaining information through attacks such as scanning, detection and social engineering. This was followed by hacking attempts (23%), which were mainly attempts to hack unauthorized hosts; and the information content security (15%), mostly being system access without verification or where information sensitivity is affected. In addition, the distribution of intelligence volume in the past year is as shown in Figure 1.
After further compilation and analysis of coordinative defense intelligence, it was found that hackers recently used Microsoft Outlook to send social engineering e-mails with the subject “Complaints Regarding Inaction of Government Officials.” The e-mails contained malicious attachments sent to government agency personnel in an attempt to deceive the recipients and plant backdoor programs to steal sensitive information. The relevant information has been provided to agencies with recommendations for coordinative defense, monitoring and protections.
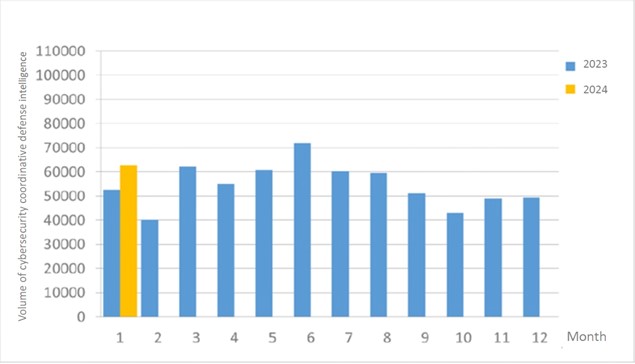
Figure 1 Statistics of cybersecurity monitoring intelligence in coordinative defense
In-process reporting and responding
There were a total of 79 cybersecurity incident reports this month (a decrease of 12 from the previous month). They were mainly related to information devices from multiple agencies connecting to seemingly malicious programs or suspected of downloading malicious programs. Such cases accounted for 58.23% of the total number of reports. In addition, the statistics of cybersecurity incident reports in the past year are as shown in Figure 2.
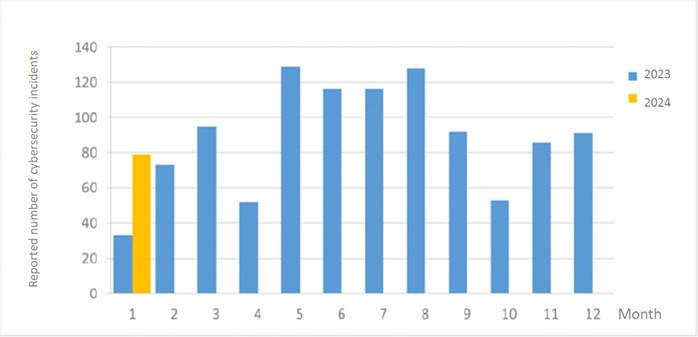
Figure 2 Number of reported cybersecurity incidents
Post information sharing
An agency's endpoint detection software (EDR) detected an attempt to upload a backdoor program to its external service website. An investigation launched by the agency found that the content management system (CMS) of the website had a weak password that allowed hackers to successfully log in and attempt to upload a malicious program. During the investigation, it was also discovered that the account password had not been changed after delivery from the vendor. The agency has deactivated the account and created a new account using a complex password (of at least eight characters in length, including English uppercase, lowercase, numbers and special symbols), as well as setting up a management interface that can only be accessed from within the agency.